
Oracle
®
Payment Interface Token Proxy Service
Security Guide
Release 6.1
E87635-01
November 2017
Copyright © 2017, Oracle and/or its affiliates. All rights reserved.
This software and related documentation are provided under a license agreement containing
restrictions on use and disclosure and are protected by intellectual property laws. Except as
expressly permitted in your license agreement or allowed by law, you may not use, copy,
reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or
display any part, in any form, or by any means. Reverse engineering, disassembly, or
decompilation of this software, unless required by law for interoperability, is prohibited.
The information contained herein is subject to change without notice and is not warranted to be
error-free. If you find any errors, please report them to us in writing.
If this software or related documentation is delivered to the U.S. Government or anyone licensing it
on behalf of the U.S. Government, then the following notice is applicable:
U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated
software, any programs installed on the hardware, and/or documentation, delivered to U.S.
Government end users are "commercial computer software" pursuant to the applicable Federal
Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication,
disclosure, modification, and adaptation of the programs, including any operating system,
integrated software, any programs installed on the hardware, and/or documentation, shall be
subject to license terms and license restrictions applicable to the programs. No other rights are
granted to the U.S. Government.
This software or hardware is developed for general use in a variety of information management
applications. It is not developed or intended for use in any inherently dangerous applications,
including applications that may create a risk of personal injury. If you use this software or hardware
in dangerous applications, then you shall be responsible to take all appropriate fail-safe, backup,
redundancy, and other measures to ensure its safe use. Oracle Corporation and its affiliates
disclaim any liability for any damages caused by use of this software or hardware in dangerous
applications.
Oracle and Java are registered trademarks of Oracle and/or its affiliates. Other names may be
trademarks of their respective owners.
Intel and Intel Xeon are trademarks or registered trademarks of Intel Corporation. All SPARC
trademarks are used under license and are trademarks or registered trademarks of SPARC
International, Inc. AMD, Opteron, the AMD logo, and the AMD Opteron logo are trademarks or
registered trademarks of Advanced Micro Devices. UNIX is a registered trademark of The Open
Group.
This software or hardware and documentation may provide access to or information about content,
products, and services from third parties. Oracle Corporation and its affiliates are not responsible
for and expressly disclaim all warranties of any kind with respect to third-party content, products,
and services unless otherwise set forth in an applicable agreement between you and Oracle.
Oracle Corporation and its affiliates will not be responsible for any loss, costs, or damages incurred
due to your access to or use of third-party content, products, or services, except as set forth in an
applicable agreement between you and Oracle.

3
Contents
Preface ...................................................................................................... 4
Audience ....................................................................................................................... 4
Customer Support ........................................................................................................ 4
Documentation ............................................................................................................. 4
Revision History ............................................................................................................ 4
1 Token Proxy Service Security Overview ........................................... 5
Basic Security Considerations ...................................................................................... 5
Token Proxy Service Security Overview ...................................................................... 5
Token Exchange Proxy Service ............................................................................. 5
Understanding the Token Proxy Service Environment ................................................ 7
Recommended Deployment Configurations................................................................. 8
Component Security ..................................................................................................... 9
Operating System Security .................................................................................... 9
Oracle Database Security ...................................................................................... 9
Oracle WebLogic Server Security .......................................................................... 9
2 Performing a Secure Token Proxy Service Installation ................. 10
Configuring for the Installation .................................................................................... 10
Installing the Token Proxy Service ............................................................................. 10
Post-Installation Configuration ................................................................................... 10
Applying Software Patches .................................................................................. 10
Configuring the Token Exchange Service ........................................................... 10
Data Purging ........................................................................................................ 11
3 Implementing Token Proxy Service Security .................................. 12
Token Exchange Service Security ............................................................................. 12
Managing Users ................................................................................................... 12
Authenticating the Service ................................................................................... 13
Using the Audit Trail ............................................................................................. 13
Appendix A Secure Deployment Checklist .................................... 15

4 Preface
Preface
This document provides security reference and guidance for the Token Proxy Service.
Audience
This document is intended for end users and system administrators installing Token
Proxy Service.
Customer Support
To contact Oracle Customer Support, access My Oracle Support at the following URL:
https://support.oracle.com
When contacting Customer Support, please provide the following:
• Product version and program/module name
• Functional and technical description of the problem (include business impact)
• Detailed step-by-step instructions to re-create
• Exact error message received and any associated log files
• Screen shots of each step you take
Documentation
Oracle Hospitality product documentation is available on the Oracle Help Center at
http://docs.oracle.com/en/industries/hospitality/
Revision History
Date Description of Change
November 2017 Initial publication

Token Proxy Service Security Overview 5
1 Token Proxy Service Security
Overview
This chapter provides an overview of the Token Proxy Service security and explains the
general principles of application security.
Basic Security Considerations
The following principles are fundamental to using any application securely:
• Keep software up to date. This includes the latest product release and any
patches that apply to it.
• Limit privileges as much as possible. Users should be given only the access
necessary to perform their work. User privileges should be reviewed periodically
to determine relevance to current work requirements.
• Monitor system activity. Establish who should access which system
components, and how often, and monitor those components.
• Install software securely. For example, use firewalls, secure protocols using
TLS (SSL), and secure passwords. Performing a Secure Token Proxy Service
Installation has more information on installing the software securely.
• Learn about and use the Token Proxy Service security features.
Implementing Token Proxy Service Security has more information on the Token
Proxy Service security features.
• Use secure development practices. For example, take advantage of existing
database security functionality instead of creating your own application security.
• Keep up to date on security information. Oracle regularly issues security-
related patch updates and security alerts. You must install all security patches as
soon as possible. Oracle’s Critical Patch Updates and Security Alerts website
has more information on security-related patch updates and security alerts:
http://www.oracle.com/technetwork/topics/security/alerts-086861.html
Token Proxy Service Security Overview
Token Exchange Proxy Service
The Token Exchange Proxy Service is a proxy interface for the hosted OPERA
application. This proxy service only processes the token or PAN exchange. The Oracle
Hospitality partner payment service providers contain the actual token functionality. As a
result, no financial transactions are exchanged and no PCI data saves in the Token
Exchange Proxy Service system.
The Token Exchange Proxy system has 3 main components:
• The Database is used to store the configuration from the web portal, and the
service will read from it
• The Token Proxy Exchange Web Portal is used to configure the settings used by
the service. It is a web application supplied in a WAR file suitable for hosting in
Web Logic. It relies on Web Logic to store some of its configuration such as the
database connection string and to provide a trusted SSL certificate for
connections from users accessing the portal.
• The Token Proxy Exchange Service is a standalone application that can be run
from a shell (or started automatically as a service in Windows). This application

6 Token Proxy Service Security Overview
creates a listener to listen on a TCP port (configured in the database but default
to 443) to listen for XML messages posted over HTTPS. This listener must be
exposed to the client (for example, Opera systems).
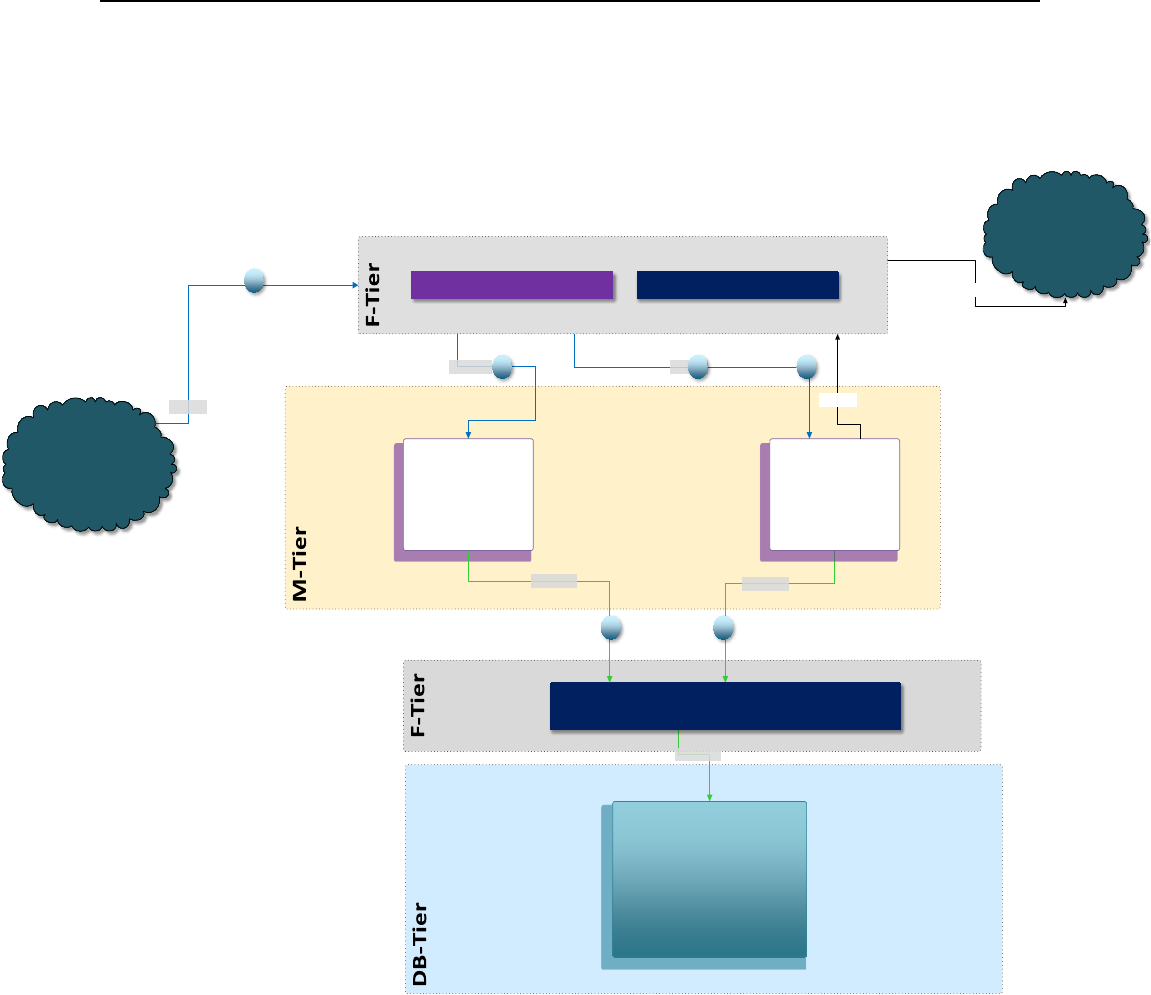
Figure 1 – Token Exchange Proxy Service Architecture
In this scenario, the hosted OPERA application and the Token Exchange Proxy Service
are both hosted in a datacenter (can be Oracle datacenter or client’s datacenter). The
applications communicate with each other using a HTTPS TLS 1.2 connection. The
Token Exchange Proxy Service communicates securely with third-party payment service
providers by using HTTPS TLS 1.2 with client certificates.
Figure 2 – Token Exchange Service Web Portal Architecture
Authorized datacenter administrators can use the Token Exchange Proxy Service web
portal to configure the service, like the merchant account and payment provider
information.

Token Proxy Service Security Overview 7
Understanding the Token Proxy Service Environment
When planning your Token Proxy Service implementation, consider the following:
• Which resources need to be protected?
o You need to protect customer data, such as credit-card numbers.
o You need to protect internal data, such as proprietary source code.
o You need to protect system components from being disabled by external
attacks or intentional system overloads.
• Who are you protecting data from?
For example, you need to protect your subscribers’ data from other subscribers,
but someone in your organization might need to access that data to manage it.
You can analyze your workflows to determine who needs access to the data; for
example, it is possible that a system administrator can manage your system
components without needing to access the system data.
• What will happen if protections on strategic resources fail?
In some cases, a fault in your security scheme is nothing more than an
inconvenience. In other cases, a fault might cause great damage to you or your
customers. Understanding the security ramifications of each resource will help
you protect it properly
8 Token Proxy Service Security Overview
Recommended Deployment Configurations
The Token Exchange Proxy Service and the configuration web portal deploys to data
centers, as described in the architecture shown in Figure 1 and Figure 2. Figure 4 shows
the deployment plan for Token Exchange Service.
Firewall
https/443
Load Balancer
https/443
sqlnet/1521
Token Exchange Proxy Service
Database
Windows 2008 R2 (x64 only)
Oracle 12c
(1) DB Instances.
• Schema for merchant configuration and
web portal user configuration
Token Exchange Proxy
Service Server
• Windows 2008 R2 (x64 onl y)
• Java JDK 1.8
Payment
Service
Providers
sqlnet/1521
Firewall
Opera via
MPLS/VPN
1
2
3
https/443
https/443
4
Token Exchange Proxy
Configuration Web
Portal
• Windows 2008 R2 (x64 onl y)
• WebLogic 12c
• Java JDK 1.8
sqlnet/1521
https/7002
6
7
Figure 3 - Token Exchange Service Network Architecture
The Token Exchange Service web portal deploys on an Oracle WebLogic server. This
Token Exchange Proxy Service runs as a windows service. The database server runs an
Oracle 12c Database. The database connection string will be encrypted and saved in
WebLogic server for Token Exchange Service web portal and in CSF for the Token
Exchange Proxy Service.
The Token Exchange Service’s listener manages its own use of the certificates provide
by the datacenter using TLS1.2, so a firewall or load balancer (if present) must not offer
any form of HTTPS to HTTP bridging functionality, and instead the connection must be
passed directly to the TokenProxy Exchange Service. The certificates provided must be
installed on all servers running the Token Proxy Exchange Service in the event the
service is installed on multiple machines for load balance or fail over.

Token Proxy Service Security Overview 9
The service will also make outgoing connections to the Payment Service Provider. This
outgoing connection will be to a URL specified by the payment service provider and the
host/port will be specified by the PSP. Port 443 is the requested and recommended
standard.
This outgoing connection can be over the internet or over VPN but must be using HTTPS
with TLS1.2 or greater. HTTPS over a VPN connection is recommended for security
reason.
Component Security
Operating System Security
The Secure Configuration of Red Hat Enterprise Linux 5 Guide and the Hardening Tips
for the Red Hat Enterprise Linux 5 Guide documents contain more information about the
operating system security.
Oracle Database Security
The Oracle Database Security Guide contains more information about the security best
practices.
Oracle WebLogic Server Security
The Securing a Production Environment for the Oracle WebLogic Server Guide from
Oracle Fusion Middleware contains more information.

10 Performing a Secure Token Proxy Service Installation
2 Performing a Secure Token Proxy
Service Installation
This chapter describes how to plan for installing the Token Proxy Service.
The Token Proxy Service Self-Hosted Installation and Configuration Guide contains more
information.
Configuring for the Installation
Before you install the Token Exchange Service, you must complete the following tasks:
• Apply critical security patches to the operating system.
• Apply critical security patches to the database server application.
• Have Java JDK 1.8 installed and Apply latest Java update
• Have WebLogic 12 c installed
Installing the Token Proxy Service
You can perform a custom installation or a complete installation. You can install using the
custom installation option to avoid installing options and products not required for your
environment. The Token Proxy Service Self-Hosted Installation and Configuration Guide
contains more information.
Installing the Token Proxy Service consists of three parts:
• Database
• Token Proxy Web Portal
• Token Proxy Service
During the database install, a database user will be created for Token Proxy Service. The
password must follow the Oracle GPS guidelines and contain:
• 8 characters
• At least 1 capital and 1 lowercase letter
• At least 1 number
• 1 special character ! " # $ % & ' ( ) * + , - . / : ; < = > ? @ [ \ ] ^ _ ` | ~
Post-Installation Configuration
This section describes additional security configuration steps to complete after Token
Proxy Service installs.
Applying Software Patches
Apply the latest Token Proxy Service patches available on My Oracle Support.
Follow the installation instructions included with the patch.
Configuring the Token Exchange Service
To configure the Token Exchange Service follow these guidelines:
• To manage the Token Exchange Service use the web portal and create a system
administrator account. Enter the user name as the employee’s email, then an

Performing a Secure Token Proxy Service Installation 11
email sends a token to enable the user to create a password. Create a password
following the Oracle GIS guidelines.
• After you create the system administrator account, you can create the other
users and clients. Use the client user accounts to configure the third-party
payment service provider connections. Define the user name and password for
basic HTTP authentication in OPERA.
• You must change the password frequently following GIS guidelines for:
o database user
o web portal user
o HTTP authentication
• The PSP Client Side Certificates expiry date will vary depending on what the
PSP set during creation of the certificate. Check the expiry date in the properties
of the certificate files. Be aware the PSP certificates will need to updating, prior to
the expiry date to avoid downtime to the interface.
Data Purging
Audit data save to database. Purge data according to the merchant’s contract policy.

12 Implementing Token Proxy Service Security
3 Implementing Token Proxy Service
Security
Token Exchange Service Security
Managing Users
Access to Token Proxy Configuration Web Portal is secured through Form-Based
Authentication. The user is required to have a valid username and password in order to
have access to the Portal.
Users are not allowed to create accounts by themselves; instead, the Web Portal
administrator will be responsible for creating the accounts and assigning the appropriate
permissions to the accounts. By default, user accounts get created without a predefined
password, instead, users will be asked to define a password when logging in for the first
time.
Token Proxy Configuration Portal uses Role-based Authorization in order to control the
access to the different areas in the web portal, a Role is basically a named collection of
privileges which can be assigned to users.
The system administrator role can access all functionality including:
• Creating or maintaining users
• Creating or modify any client
• Maintaining the card type translation
• Viewing or maintaining the audit logs
A client user can only log in and manage existing clients that they are specifically
assigned to by a system administrator user. The client user role cannot create or view the
details of other clients.
The Security mechanism in Token Proxy Configuration portal implements the following
features:
• You must use an email as the user ID for the Token Exchange Service web
portal.
• Create passwords using a reset password link containing a unique random token
sent by email.
• The database stores passwords using a salt hash format. The hash algorithm is
PDKDF2WithHmacSHA256, using a password based key derivation function 2.
• The salt is a randomly generated 16byte value using the secureRandom Java
class. The algorithm for this is SHA1PRNG.
• The hash mechanism specifies an iteration count number defining the number of
hashing rounds.
• The user record in the database contains the final password hash, salt, and the
hash algorithm name and the iteration count.
• All password values are validated to ensure they meet the required minimum
complexity.
• The system administrator and the client user roles are created during the
installation.
• Configurable password expiration (default value: 90 days)
• Configurable account locking mechanism based on failed logging attempts
(default: 3 failed attempts, default lock time: 240 minutes)

Secure Deployment Checklist 13
• Configurable Password History validation ( users will not be able to repeat
passwords used in the past, default: last 4 passwords)
• One-time-token-based reset password mechanism with configurable token
expiration time (default: 24 hrs.)
Authenticating the Service
The connection to Token Proxy Exchange Service is secured using Basic HTTP
authentication over SSL (TLS 1.2 or later). Any client application interacting with Token
Proxy Service will need to present a username and password in the HTTP Authorization
header of the requests (in base64 encoding format), Token Proxy Service will then
validate the credentials presented by the client application/system and proceed to accept
or reject the message according to outcome of the validation process.
The authorization credentials that the client application or system will use to
communicate with Token Proxy Service are defined in Token Proxy Web Portal, these
credentials (password) are stored in a salted-hashed form in Token Proxy DB to be used
during the Client Authentication phase
The communication between Token Exchange Proxy Service and the Payment Service
Providers is secured by using Certificate-based Mutual Authentication. That is, while a
server side certificate is expected to be deployed at PSP (server side) for HTTPS
communication, PSP is also expected to provide a client side certificate to be deployed at
Token Proxy Service side. Token Proxy Service will present this client certificate during
HTTPS communication with PSP so that PSP can authenticate the service properly.
The mechanism is based on the following actions:
1. Token Proxy Service sends a requests to the Payment Service Provider(PSP)
2. PSP presents its certificate to Token Proxy Service
3. Token Proxy Service verifies the PSP certificate
4. If successful, Token Proxy Service sends its certificate to the PSP
5. PSP verifies the Token Proxy certificate
6. If successful, PSP accepts the requests, process it and sends the response back
to Token Proxy Service
Note: The PSP Client Side Certificates expiry date will vary depending on what the PSP
set during creation of the certificate. Check the expiry date in the properties of the
certificate files. Be aware the PSP certificates will need to updating, prior to the expiry
date to avoid downtime to the interface.
Using the Audit Trail
Token Proxy Configuration Portal also features an Auditing mechanism that allows to
keep record of actions performed by users, actions such as:
• Successful user login/logout
• Failed user logging attempts
• Configuration updates
• Authorization/Authentication updates
The system records the configuration changes as the before and after states and records
the data in the audit log table by serializing the record into a JSON string. All passwords
hashes are stored in binary format and excluded from the serialization process. Using the
Token Exchange Service web portal, you can view the audit records and export the audit
records to a spreadsheet.

14 Implementing Token Proxy Service Security
The audit records save in the database for a minimum of 90 days. The Auditing
mechanism allows exporting the data from Database into .xls files for long term storage
or, for analysis with tools such as Splunk. You can manually purge the audit records from
the application. Purge data according to the merchant’s contract policy.

Secure Deployment Checklist 15
Appendix A Secure Deployment
Checklist
This appendix lists actions that need to be performed to create a secure system. The
following is an example:
The following security checklist includes guidelines that help secure your database:
• Install only what is required.
• Lock and expire default user accounts.
• Enforce password management.
• Practice the principle of least privilege.
o Grant necessary privileges only.
o Revoke unnecessary privileges from the PUBLIC user group. iii. Restrict
permissions on run-time facilities.
• Restrict network access.
• Apply all security patches and workarounds.
o Use a firewall.
o Never poke a hole through a firewall.
o Protect the Oracle listener.
o Monitor listener activity.
o Monitor who accesses your systems.
o Check network IP addresses.
